🧑🏫My Methodologies
description: For Personal Reference
Gathering Breached Credentials
file upload vulnerability test
Common Ports for a web Application:
Set domain scope (burpsuite)
XSS recon methodology
▶ cat domains.txt | waybackurls > urls
KXSS
The vulnerable parameter for XSS should have Unfiltered : [“ ‘ < > $ | ( ) ` : ; { } ]
Payload:
any name tag xss payload:
Bypass Waf Pyaload:
Open Redirect Mass Hunt
tool = ragno, qsreplace
Example: One Liner for Hunting Mass Open Redirect
Amass Command
Detect Low Hanging Bugs and Sensitive Information like API Keys, Secrets etc. including JS Files and HTML Pages
First run Amass Scan and save its output and then run Sublist3r with bruteforce mode and also save its output in different file. Now open a Website such as https://www.textfixer.com/tools/remove-duplicate-lines.php to remove duplicate subdomains.
Tool: https://github.com/BitTheByte/Eagle
Basic Usage:
Advanced Usage:
To check API keys if they vulnerable or not, use a tool such as gmapsapiscanner, it is usefull to save the time by automating the process and also if it gets any Vulnerable API, it will generate its POC itself.
Tool: https://github.com/ozguralp/gmapsapiscanner
Usage:
SQL Injection Methodologies
*try login with admin admin and send login request to burp
*do an active scan
if show SQL injection with parameter
#POC
copy request in txt
and on sqlmap
and you have a valid SQL INJ 😎😎
SQL Injection Auth Bypass:
Blind SQL Injection payload:
Reflected XSS On private program
1-
2-
3-
DONE 😎
Find SQL injections (command combo)
Here’s what’s going on in detail:
First we will find all subdomains under our target domain.
Next we will identify all alive web servers running on those subdomains.
Waybackurls will fetch all URLs that the Wayback Machine knows about the identified alive subdomains.
Now we will filter out URLs that match patterns with potential SQL injection.
The final step is to run sqlmap on all identified potentially vulnerable URLs and let it do its magic.
Protip: If you need to bypass WAF (Web Application Firewall) in the process, add the following options to sqlmap:
Get scope of Bugcrowd programs in CLI
There is a new tool in town called bcscope which can get you the scope of all bug bounty programs available on Bugcrowd platform, including the private ones.
All you have to do is to provide your Bugcrowd token like this:

Quite convenient and pretty useful!
Get the tool here:
https://github.com/sw33tLie/bcscope
Chaining file uploads with other vulns
When testing file upload functionalities in a web application, try setting the filename to the following values:
../../../tmp/lol.png —> for path traversal
sleep(10)-- -.jpg —> for SQL injection
.jpg/png —> for XSS
; sleep 10; —> for command injections
With these payloads, we may trigger additional vulnerabilities.
GitHub dorks for AWS, Jira, Okta .. secrets
Here are some useful GitHub dorks shared by @hunter0x7 for identifying sensitive information related to Amazon AWS cloud:
Here’s another list of GitHub dorks shared by @GodfatherOrwa for identifying various other credentials and secrets:
Protip: While you are doing GitHub dorking, try also GitDorker (made by @obheda12) which automates the whole process and which contains 400+ dorks in total, for easy bug bounty wins.
Detailed information about GitDorker can be found here.
Also check related tip BBT5-8.
Simple reflected XSS scenario
Here’s an interesting bug bounty write-up leading to a reflected XSS (Cross-Site Scripting by visiting a link).
The author was able to successfully identify and exploit XSS despite the fact that the application was filtering some characters and keywords (possibly protected by WAF).
Here’s what @_justYnot did in detail:
Run subfinder -d target.com | httprobe -c 100 > target.txt
Run cat target.txt | waybackurls | gf xss | kxss
Got a URL which had all the special characters unfiltered and the parameter was callback=
Tried some basic XSS payloads but they weren’t working, the site was filtering some keywords in the payload (like script and alert)
Then he referred to the @PortSwigger XSS cheat sheet (link)
After trying some payloads, one payload with event as onbegin worked and XSS executed successfully!
Made a good report, sent it to the company last month and got rewarded $$
This is a perfect example why we should never give up when things get difficult. When you’ve got a lead, you have to keep pushing to get the reward! Here’s list of tools @_justYnot used:
https://github.com/projectdiscovery/subfinder
https://github.com/tomnomnom/httprobe
https://github.com/tomnomnom/waybackurls
https://github.com/tomnomnom/gf
https://github.com/1ndianl33t/Gf-Patterns (xss pattern)
https://github.com/tomnomnom/hacks/tree/master/kxss
XSS firewall bypass techniques
Here’s a list of 7 useful techniques on how we can bypass WAF (Web Application Firewall) while exploiting XSS (Cross-Site Scripting) in a web application:
Check if the firewall is blocking only lowercase:
Try to break firewall regex with new line (\r\n), aka. CRLF injection:
Try double encoding:
Testing for recursive filters, if firewall removes the text in bold, we will have clear payload:
Injecting anchor tag without whitespaces:
Try to bypass whitespaces using a bullet:
Try to change request method (POST instead of GET):
GET /?q=xss POST /q=xss
Try capatalizing alert function:
Short XSS Payload:
Hex XSS Payloads:
Throw this into EVERY parameter you see
by @theXSSrat
Nuclei CVE-2023-24488 Citrix XSS - Easy Bug Bounty
Command: subfinder -d target.com -silent | nuclei -t http/cves/2023/CVE-2023-24488.yaml assetfinder target.com | nuclei -t http/cves/2023/CVE-2023-24488.yaml Template: XSS nuclei template CVE-2023-24488.yaml Shodan Dork: ssl:target.com title:"Citrix gateway" Dork: intitle:"Citrix Gateway" -site:citrix.com
Some awesome people on twitter
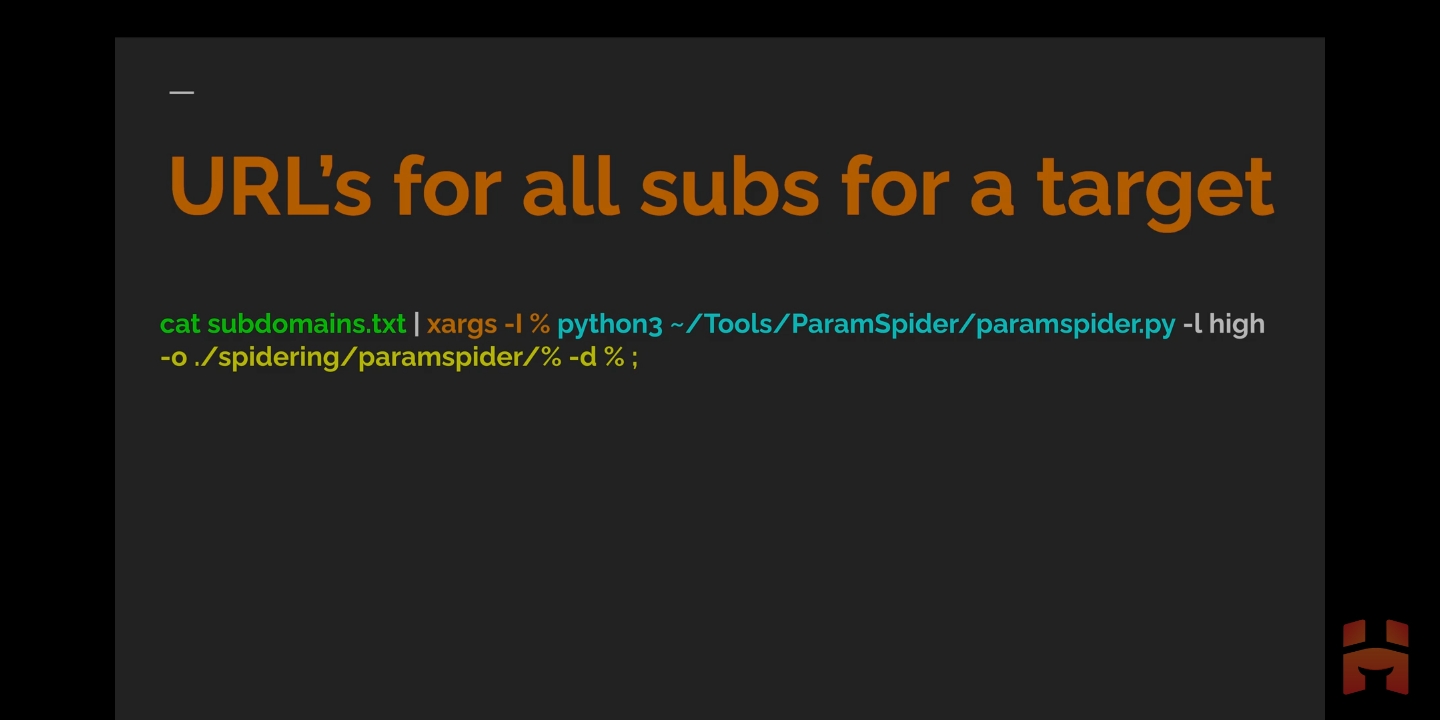
Find all Subdomains in a Single Shot
VHOST Fuzzing using FFUF
Directory Fuzzing using FFUF
Feroxbuster directory fuzzing
Check all methods on domainlist for Information Disclosure
Path based xss with different type methods.
Inject payload in every path and check xss
append fake paramters in every path and check xss vulnerability
made poc for you in your terminal
Find Blind RCE with automation
If you get Response of your burp collab! Boom RCE
Scan open ports of domain list using masscan
Easy way to find Path based XSS
Where to look for Blind XSS
Review Forms
Contact Us pages
Password Field (you never know if the other side doesn't properly handle input and if your password is in view mode)
Address fields of e-commerce sites.
First or last name field while doing credit card payments
Set User-Agent to Blind XSS payload. You can do that easily from a proxy such as Burpsuite. And there are many more cases, but we would encourage you to read some reports to get a perfect knowledge, where other hackers are already applying these techniques and how you can use them in your program
Find Google map API keys in JS files & endpoints from Domains & Subdomains.
Find P1 Bug in a minute
For Checking SSTI Vulnerability..
Output: https://example.com/?s=ssti{{7*7}} -> ssti49 --> Means Vulnerable
Check sqli Vulnerability in One shot of domains & subdomains
Find xmlrpc in single shot on domain & subdomains.
Output: https://example.com -> XML-RPC server accepts POST requests only
JSFScan.sh usage
XSS Normal test input
Mobile App Testing Guide:
Android: Intercept traffic with BurpSuite.
Find hidden GET parameters in JS files
Get Reverse Shell:
Depixelate images
Reverse shell using ZIP file:
the code in this:
Opposite to Keyhacks -> nokeyhacks:
Increase XSS vulnerability impact
Mindmaps for Penetration Testing


Last updated